Newer Intel Chipsets with vPro/Intel AMT, such as the Q57, Q67 and C206 (as long as they’re paired with a Core i5/i7 or Xeon with integrated graphics), have a feature called Remote KVM.
To use it, press Ctrl-P at the BIOS splash screen to get to the MEBx menu, set a password (minimum 8 characters, mixed case, numbers and special characters are enforced), configure the network settings (they can even match the OS’s IP address), enable Remote KVM and disable User Opt-In.
Next, download the Intel AMT SDK, extract the ZIP and open .\Windows\Intel_AMT\Bin\KVM\KVMControlApplication.exe . There, you can enable KVM as seen in the following screenshot:
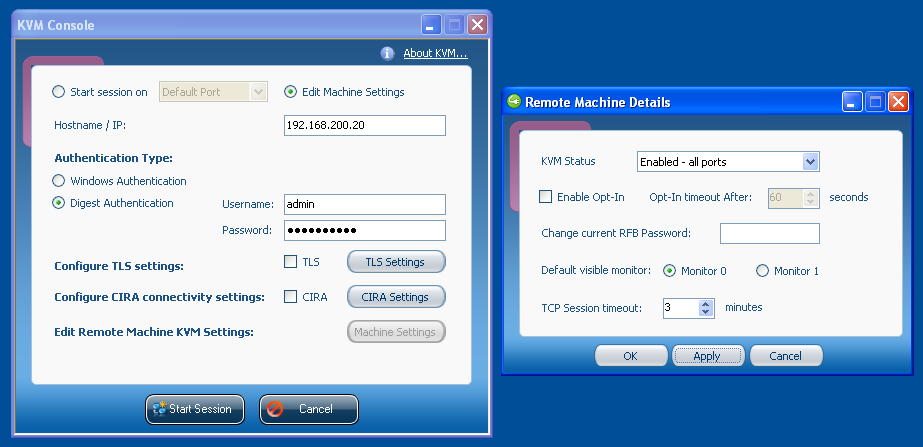
KVM Status can either be set to “redirection ports” (meaning it will only be accessible to VNC clients that specifically support Intel AMT, such as RealVNC Viewer Plus or Intel’s KVM Console, the former of which costs $100, the latter of which constantly overlays a RealVNC logo on the screen), to “default port” (meaning it will be accessible on TCP port 5900 to any VNC client), or to “all ports” (which is the combination of both).
If you enable VNC access, you will also need to set an RFB Password. As I found out the hard way (Intel actually has it hidden in their documentation as well), it gets truncated at 8 characters and at the same time has the same security requirements as the general AMT password.
If you disabled User Opt-In in the MEBx menu, you can disable it here as well.
So that’s it, now you can use almost any VNC client you like (RealVNC and Chicken of the VNC work fine, while Apple Remote Desktop appears to cause the VNC server to freeze) and control the machine just as if you were sitting in front of it.
Two things I noticed: On my machine, the BIOS splash screen was not visible during a KVM connection (not even on a directly-attached screen), so to get to the BIOS I needed to blindly hit the corresponding key. Also, it is not possible to enter the MEBx menu during a KVM connection (probably for some obscure security reasons): if you hit the corresponding key, it immediately exits and continues normal bot; if you establish a KVM connection while in MEBx, you get disconnected immediately.
After about half an hour of playing with Intel AMT, I have to say it’s really cool. If you’re buying/building a home server, you should definitely consider getting a mainboard with Intel AMT 6.0 or later: You get server-grade remote management capabilities for a very small premium, which are very useful if you ever lock yourself out while remotely connected to the server.
Thanks!
Oh and btw – you need to copy those 3 .dll files from bin64 folder into main KVM folder if you want to lauch that Console on a 64bit machine 🙂
Pingback: Intel V-pro techology
Pingback: Erste Erfahrungen mit vPro « alexunil Ltd.
Sorry, I can’t download Intel AMT SDK usung that link upside.
Could You share it to any web fileserver (such as rapidshare or depositfiles)?
Thanks for sharing this!
I can now happily use a plain VNC viewer from Linux and a web interface on port 16992 to control power if needed. Good tip on the password length limitation.
Cheers.
Pingback: VMware ESXi 5.5.0 panics when using Intel AMT VNC « Michael Kuron's Blog
Pingback: vPro what is it and can I use it or can someone else?
Note that you must use the built-in graphics! Note an external card in your pci-e port.
If anyone’s having issues where the connection instantly drops with regular VNC clients, downloading the 32-bit version of RealVNC from their website seems to work. I couldn’t get a 64-bit RealVNC, TightVNC or Remmima to work under Linux.
For search engines, the error I get is:
xvncviewer: read: Connection reset by peer
Pingback: Intel AMT gives 401 Unauthorized when trying to login - TecHub
Pingback: Intel AMT gives 401 Unauthorized when trying to login – Blog SatoHost
KVMControlApplication.exe is no longer part of the SDK-kit
You have another, updated solution or link to an older version of SDK-kit?
Regards, Lars.